In this article I will go through the steps required to install and configure Duo Security with Ubuntu Server for two factor authentication. This can be adapted to apply to SSH log-ons, sudo access, etc. The Linux PAM (pluggable authentication modules) make this easy to implement and customise.
I currently have this implemented on my Ubuntu 14.04 x64 LTS Server and it works really well.
Prerequisites
We need to add the Duo Security repository to your sources, import the GPG key, refresh the apt-get cache then install the duo-unix package.
Note: Replace trusty with precise if you’re running Ubuntu 12.04
echo 'deb http://pkg.duosecurity.com/Ubuntu trusty main' | sudo tee /etc/apt/sources.list.d/duosecurity.list curl -s https://duo.com/APT-GPG-KEY-DUO | sudo apt-key add - sudo apt-get update sudo apt-get install duo-unix
Now we need to run through a few pages on the Duo website to get the integration keys.
- Log-in to the Duo Security admin page
- Click Applications –> Protect an Application

- Scroll down to Unix Application and click Protect this Application
- Make a note of your integration key, secret key and API hostname.
Configuration
First we’ll need to edit the pam_duo.conf file and plug in your integration key, secret key and api hostname.
Note: there are more options available here – for example defining what you want to happen if the Duo Security servers are unavailable (by default it will bypass 2FA but you can force it to deny log-on).
sudo nano /etc/duo/pam_duo.conf
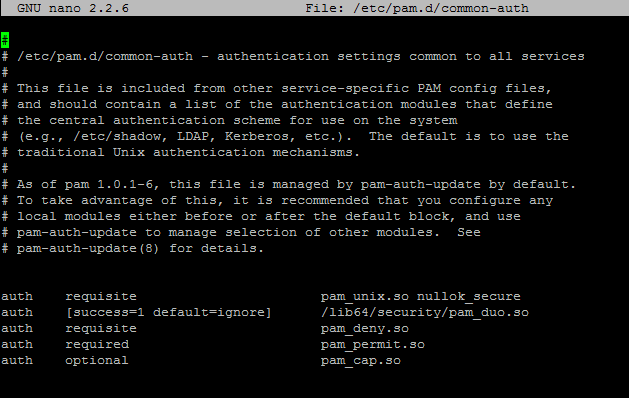
Now we want to edit the PAM common-auth file to require 2FA from the pam_duo.so module.
sudo nano /etc/pam.d/common-auth
Your config should look like the below – note that I took out the comments so that it is easier to read.
auth requisite pam_unix.so nullok_secure auth [success=1 default=ignore] /lib64/security/pam_duo.so auth requisite pam_deny.so auth required pam_permit.so auth optional pam_cap.so
sudo nano /etc/ssh/sshd_config
Set the following variables:
ChallengeResponseAuthentication yes UsePAM yes UseDNS no
A few more steps for public key authentication
If you’re using public key authentication then set the following variables in sshd_config:
PubkeyAuthentication yes PasswordAuthentication no AuthenticationMethods publickey,keyboard-interactive
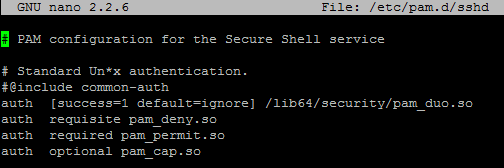
Also you need to make some changes in the pam.d/sshd config
sudo nano /etc/pam.d/sshd
You need to comment out and add the following lines:
#@include common-auth auth [success=1 default=ignore] /lib64/security/pam_duo.so auth requisite pam_deny.so auth required pam_permit.so auth optional pam_cap.so
It should look like this:
Final thoughts…
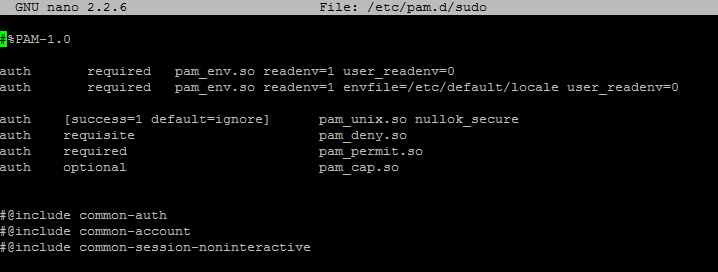
By default you will be prompted for 2FA on log-on (obviously). By default you will also be prompted for 2FA when you run sudo – everytime. If you don’t want this to happen then have a look at the /etc/pam.d/ directory.
Here you will find PAM authentication tasks. You will find one for sudo. If you edit that file to look like the below, you will only be prompted for your password and not 2FA.
Again it all depends on your environment and how you want things set-up vs convenience vs security.