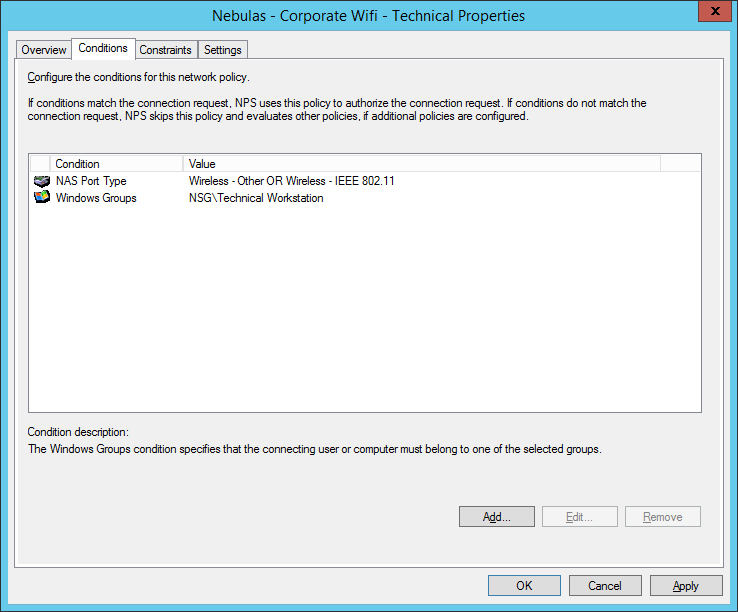
The below is more of a supplement to the Meraki knowledge base articles as I thought (personally) they were lacking quite a bit with some important information – also a warning about using group policies in the Meraki dashboard.
The main articles to follow are:
- RADIUS: Configuring PEAP-MSCHAPv2 – Machine Authentication
- RADIUS: Creating a policy in NPS to support PEAP-MSCHAPv2 – Machine Authentication
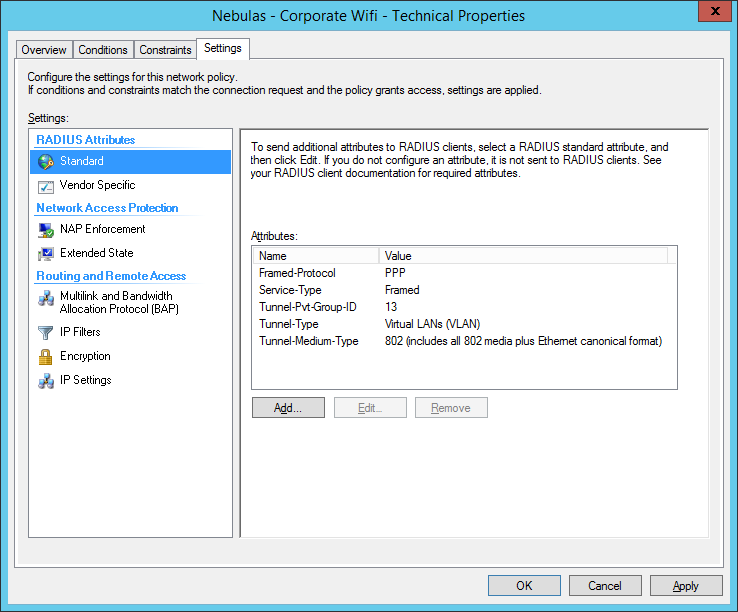
Basically you have something like this:
The above attributes are required if you want to send the VLAN tag in the RADIUS response. See this article for more information.
NOTE: As of this post there exists an issue (and this issue has been in existence for about 6 months now – I have been struggling to find a solution to the horror in Windows that is seeing the wireless network in ‘limited connectivity’ mode) where Pairwise Master Key caching (PMK) fails to work properly and causes the VLAN policy tag to be lost during client re-association.
This issue only exists if you use VLAN assignment in the group policy section in the Meraki dashboard. If you use the above steps to send the VLAN tag as part of the RADIUS response then you will be fine.