MineMeld is an “extensible Threat Intelligence processing framework and the ‘multi-tool’ of threat indicator feeds. Based on an extremely flexible engine, MineMeld can be used to collect, aggregate and filter indicators from a variety of sources and make them available for consumption to peers or to the Palo Alto Networks security platforms.”
It was recently open-sourced by Palo Alto and can be found on Github.
Essentially it can be used to grab IP/URL/Domain feeds from anywhere on the internet (a miner), aggregate and process the feed or feeds using regex if necessary (a processor) and output them in a format suitable to use in an External Dynamic List object on a Palo Alto firewall.
Technically the outputs can be used for anything you want but they work with dynamic lists on the Palo Alto’s out of the box.
I’ve only used MineMeld for a few weeks but I have a few feeds configured – I’ll go through the configuration of one of them now. It’s pretty straight forward but hopefully it’ll come in handy.
Blocking Tor Exit Nodes
In this example we’ll do the following:
- Configure the tor exit node (miner)
- Configure an aggregator (processor)
- Configure the output in a format suitable for your PAN firewall (output)
- Configure a new External Dynamic List (EDL) object on your Palo to look for the output you created in MineMeld
- Create a new security policy on the firewall to block outbound access to the Tor exit nodes.
- Confirm the EDL object on the firewall is being populated
- Confirm that traffic to Tor exit addresses are indeed being blocked
Let’s get started… if you don’t have MineMeld set-up already then you should probably do that first before continuing! You can download the .ova so you can use it in VMware (I have it set up on VMware workstation at the moment) or install it manually on Ubuntu (installing it manually is probably best for a production environment)
- First let’s configure the Tor miner. This essentially sets up a process in MineMeld to go and grab the list of Tor exit nodes. Tor makes this information available publicly. As you can see, the format is not suitable for import just yet.Click Config in MineMeld. You’ll see a bunch of default miners, processors and outputs. I deleted all of them as they weren’t useful for me.
Click the Add button and give the miner a useful name. From the prototype dropdown select tor.exit_addresses. There are no inputs. Click Save.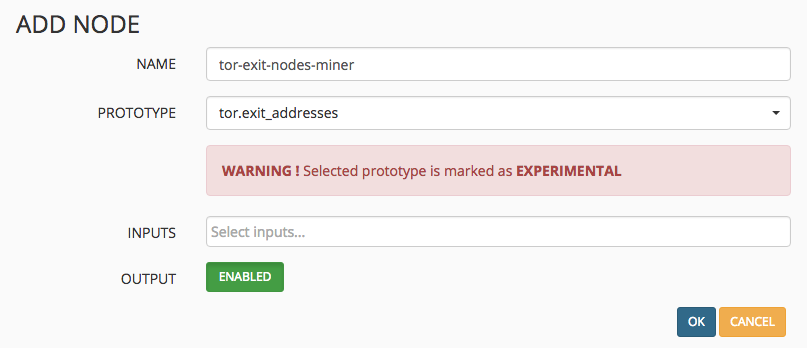
- Now we want to set up a feed aggregator/processor. Click the Add button again and this time choose the processor stdlib.aggregatorIPv4Generic
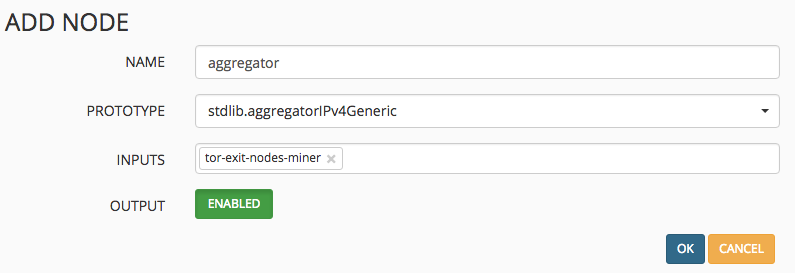
- Lastly we want to create an output. This is essentially a clean, formatted version of the raw IP addresses we saw in step 1. Click the Add button and give the output an appropriate name and select stdlib.feedHCGreen from the dropdown. Make sure you select the processor/aggregator as the input.
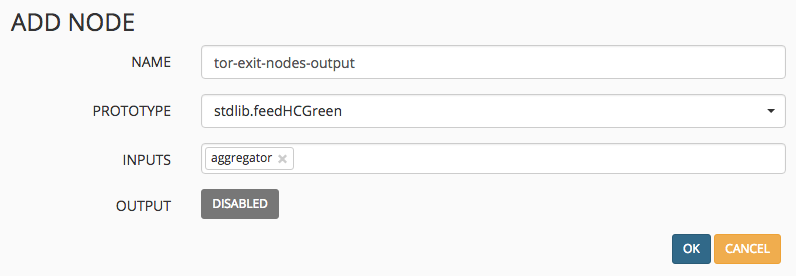
- Commit the changes by clicking on the Commit button on the top left of the Config screen. Within a few minutes your Nodes page should look like the below. Don’t forget that if you are blocking the app-id tor on your Palo, MineMeld won’t be able to get the IP address list from the tor web server!
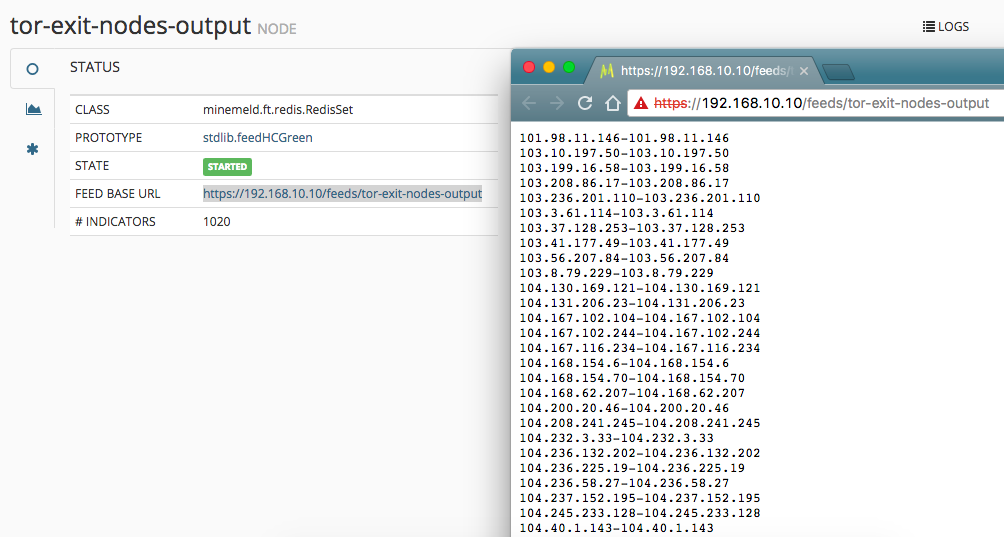
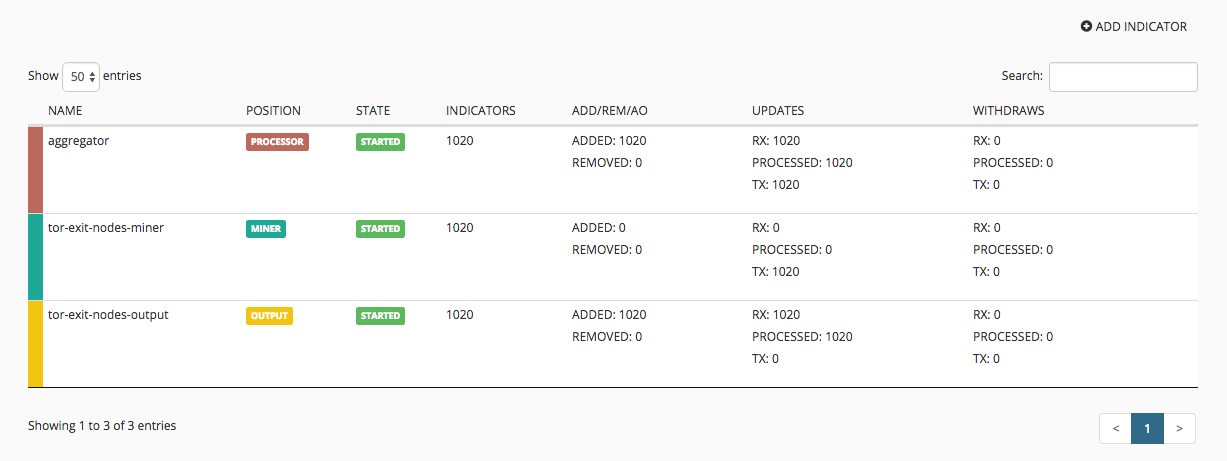 If you click the tor-exit-nodes-output, you’ll see a feed base url field with a direct link to the feed which is now hosted on your MineMeld server. This is what we’ll use in the Palo next.
If you click the tor-exit-nodes-output, you’ll see a feed base url field with a direct link to the feed which is now hosted on your MineMeld server. This is what we’ll use in the Palo next.
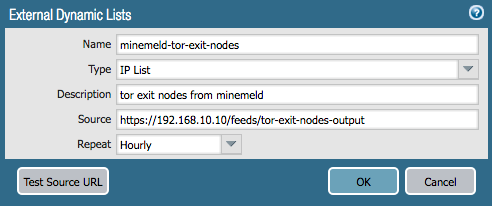
- Now let’s create an External Dynamic List object on the firewall. Click Objects then External Dynamic List. Click Add and fill in the details – the most important is the feed url which is the one we looked at just above. Click Test Source URL which should report back a success message. If it doesn’t then ensure your Palo can access your MineMeld server).
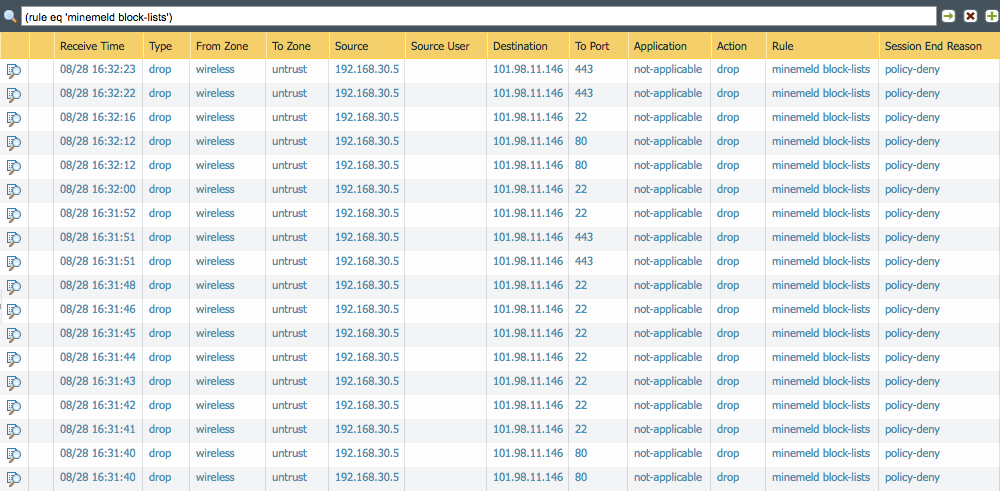
- Now we’ll create a security policy that will block all outbound access to this dynamic list; aka Tor exit node IP’s. Create a security policy as you normally would but this time put the new external dynamic list as a destination address. For example:

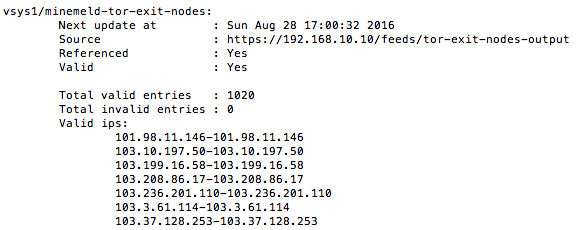
- Now we want to make sure the EDL is being populated correctly on the firewall. Log-in to the CLI and run the following command:
request system external-list show type ip name minemeld-tor-exit-nodes
You should see something like this if the firewall is successfully pulling the information down from your MineMeld server.
- Finally… time to test the block list to make sure we’re actually blocking requests to the Tor exit nodes. I attempted to initiate a few requests to a Tor exit node via http, https and ssh. As expected, they were all blocked by the firewall: