This article will serve as a quick tutorial on installing and configuring fail2ban on an Amazon EC2 instance.
I like to think of fail2ban as a ‘second line’ of defence against systematic attempts to break through and access SSH on a server.
First line of defence should always be disabling the root log-in, using strong passwords/using private keys for log-on, etc.
It can do a lot more than protecting against brute-force SSH attacks using regex’s but that is not in the scope of this tutorial.
Installation
I am assuming the instance you want to install fail2ban on is the default Amazon Linux AMI. If you are using another Linux distribution, the syntax to some of the commands listed below may be slightly different.
sudo wget http://downloads.sourceforge.net/project/fail2ban/fail2ban-stable/fail2ban-0.8.4/fail2ban-0.8.4.tar.bz2?use_mirror=kent
sudo tar -xjvf fail2ban-0.8.4.tar.bz2
cd fail2ban-0.8.4
sudo python setup.py install
sudo cp files/redhat-initd /etc/init.d/fail2ban
sudo chkconfig --add fail2ban
sudo chkconfig fail2ban on
sudo service fail2ban start
Configuration
There are some important parameters that you should understand and set before leaving fail2ban to do its thing.
The figures below should be set by someone who understands the system well and what it is used for (hopefully you). For example, if you have hundreds or thousands of users, you don’t want to set the ban limit too low, otherwise you will undoubtedly receive many complaints from users entering their passwords incorrectly 🙂
The following parameters can be found in the jail.conf (or jail.local file) found @ /etc/fail2ban:
- ignoreip – Set your own IP address here so that you don’t accidentally lock your self out! (a DNS host would be better if you are on a dynamic IP)
- bantime – the number of seconds an IP address is put on the ‘ban list’
- maxretry – Number of failed attempts before banning the IP address
- findtime – If maxretry attempts made within findtime seconds, then ban IP address. For example; if findtime is 600 seconds and maxretry is 3… a user will be banned if they make 3 attempts within 10 minutes. If they make 2 attempts in 9 minutes and make the 3rd 5 minutes later; they will not be banned.
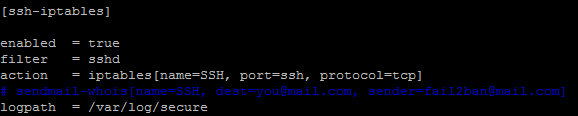
You also want to set the ‘enabled’ parameter to true under [ssh-iptables]
Also, if you have not configured sendmail on your server or you do not want fail2ban sending mail, just comment out the line beginning with sendmail-whois with a # (hash symbol)
Last but not least, change the logpath to the path where the security log is stored. On the Amazon Linux AMI’s, this is stored @ /var/log/secure
After making these changes, you should restart the fail2ban service:
service fail2ban restart
Optional
I like to have my fail2ban logs (these are internal fail2ban logs such as which IP addresses have been banned and unbanned) write out to the same directory as where the configuration files are stored. If you would like to change the location of the fail2ban log files, simply open up the fail2ban.conf found @ /etc/fail2ban/ and change the logtarget parameter.
Uninstallation
If you want to remove the fail2ban package, simply execute the following:
sudo service fail2ban stop
sudo chkconfig fail2ban off
sudo rm -rf /etc/fail2ban
sudo rm /etc/init.d/fail2ban
sudo rm /var/log/fail2ban*