This is my first in, I hope, a series of posts about the ‘state of things on the internet’ along with my findings and anything interesting I may have come across along the way.
This post will be about the state of Telnet (Port 23) on the internet from the perspective of a single internet-scanning host (read more in the methodologies section below). I’ll be going through some statistics including: top countries, top brands and/or firmware and lastly, an analysis on banner responses.
Scanning/Results Methodology
First let’s get some basics out the way so that it is clear how I got the results I did from my scans:
- I used a Kali Linux distro running in a VM – the performance and reliability could have been better running this on a physical machine with direct access to the NIC; maybe next time.
- I used masscan as the port scanner and banner grabber – it’s very similar to Nmap in terms of usage but it can scan at an order of magnitude faster than Nmap. The below is a copy of my masscan.conf which I used to run the scans:
rate = 6000.00 output-format = grepable ports = 23 range = 0.0.0.0-49.255.255.255 exclude-file = /root/Desktop/ip-exclude-list.txt randomize-hosts = false banners = true adapter-ip = 192.168.10.200 output-filename = /root/Desktop/masscan-results/0.0.0.0-49.255.255.255-original.txt wait = 30
I could get to about 6,000 packets per second before melting my connection; in fact at one point the data plane on my (enterprise level!) firewall/router crashed so I lost about 15 minutes of data whilst it was busy restarting.
I scanned blocks at a time to keep the results manageable.
The exclude file is a list of the RFC1918 addresses.
- I ran these scans off an internet connection with the following speeds:
73Mb/s receive and 19Mb/s transmit. - Results were analysed in Excel 2016 x64 – that last bit is important… a 32 bit version of Excel would cry about not being able to address more than 2GB of memory. Also it turns out analysing more than a million rows in Excel can be made a lot easier by using the Power Pivot tools which I didn’t know about previously
- I used an awesome free service/API called ip2c.org (IP-2-Country) which allows one to pass an IP address in and get a Country code back. My PowerShell script to grab this data:
$csv = Import-Csv '.\0.0.0.0-49.255.255.255-original.txt' -Delimiter "`t" -Header "Host","Port","Service","Banner"
$export = "0.0.0.0-49.255.255.255-countries.csv"
ForEach ($row in $csv)
{
$Matches = $null
$regex = (Invoke-WebRequest "http://ip2c.org/$($row.Host)").content -match ('[0-1];[A-Za-z]*;[A-Za-z]*;(.*)')
$row | Add-Member -MemberType NoteProperty -Name Country -Value $Matches[1]
$row | Export-Csv -Delimiter "," -Path ./$export -Append -NoTypeInformation
}
Lastly, I want to make two things clear about the #numbers in my results:
- There are probably/most likely a lot more (hundreds of thousands/millions?) more devices out there then I found – I may need to adjust my scan rate the next time I run such a test so that I capture more data and also I’d probably run my next test on physical hardware so that masscan has direct access to the NIC.
- There are more open Telnet ports than there are banners – that’s normal for a number of reasons. Some devices simply won’t return a banner. Some will respond to a probe even if nothing is listening behind it – think security appliances (SYN cookies) and load balancers.
Results
Open Ports vs Banners Received
A total of 5,601,277 hosts were reported to be listening on Port 23. Of these, 2,570,080 (46%) returned banners.
It’s common to see load balancers and security appliances reply back to a probe on Port 23 (or any other port really) which is probably one of the reasons why there are so many more open ports than banners received. The analysis below is based on the 2,570,080 hosts where banners were received from the scanned hosts.
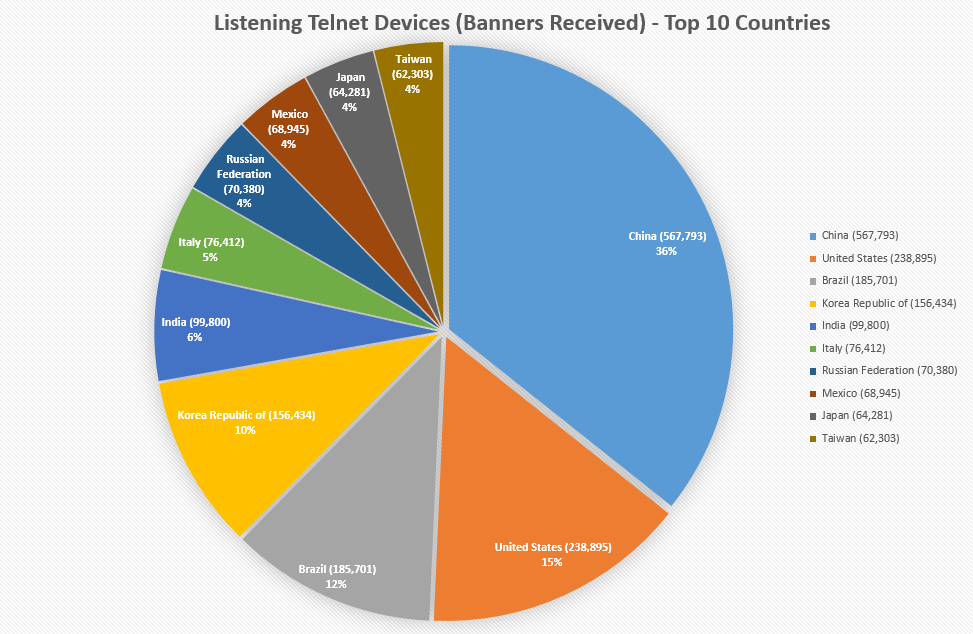
Top 10 Countries
The chart below is of the top 10 countries where banner headers were received – i.e., from a total of 2.5 million hosts.
The first few loosely follow the order of population by country so it’s no surprise to see China at #1.
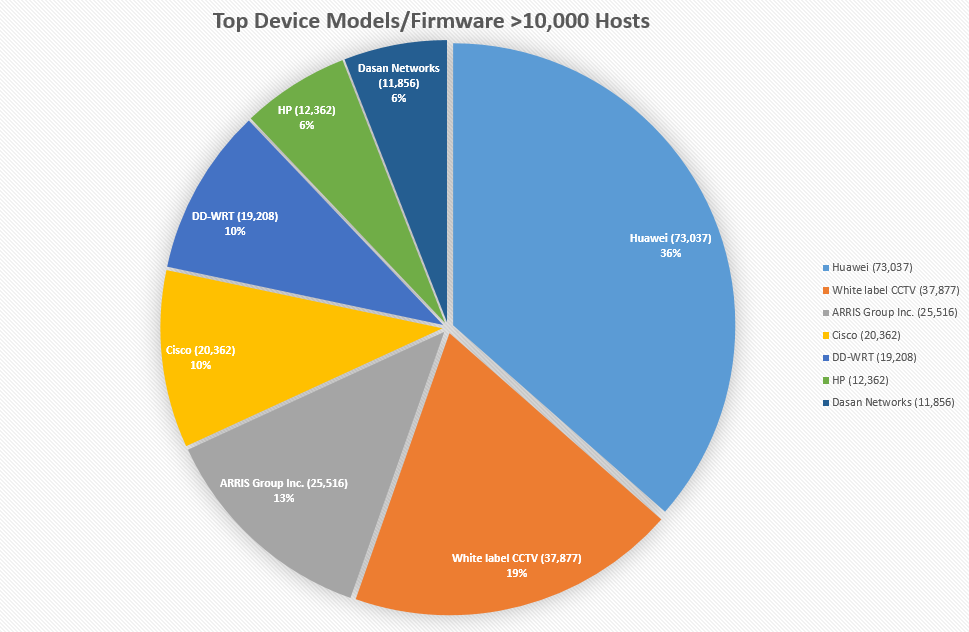
Top Models/Firmware
Analysing banner responses for long periods of time can make anyone go insane but it can also make one good at spotting patterns such as sentence structures which make it highly likely that multiple devices belong to the same manufacturer.
It’s no surprise to see Huawei devices pop up the most in my scans; they manufacturer networking and telecommunications equipment – apparently the largest in the world with regards to the latter.
The white label CCTV is an interesting one – it’s the only name I could come up with because as far as my research takes me, it seems like generic CCTV/IP camera/Digital Video Recorder firmware that has been re-purposed by X number of manufacturers.
The web page for this firmware looks like the below – you may have seen it before, I know I have.
The banner for this firmware typically looks like this:
\x0a\x0aSorry, Dear! telnet service is still in lock-time,\x0d\x0aYou have to wait X min Y sec,\x0d\x0aIf you have any problem, ask administrator for help.\x0d\x0a
I was surprised to see so many DD-WRT firmware enabled routers with open Telnet access as this firmware is typically installed by tech enthusiasts and more advanced users who should probably know better than to enable Telnet on the external interface. DD-WRT helpfully gives us the firmware release and system name in the banner which can be useful for an attacker looking for interesting victims…
\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\x0d\x0d\x0aDD-WRT v24-sp2 big (c) 2012 NewMedia-NET GmbH\x0d\x0aRelease: 04/07/12 (SVN revision: 18946)\x0d\x0a\x0d\x0aCIA Surveillance Node login:
\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\x0d\x0d\x0aDD-WRT v24-sp2 giga (c) 2013 NewMedia-NET GmbH\x0d\x0aRelease: 03/25/13 (SVN revision: 21061)\x0d\x0a\x0d\x0aVolkswagen WiFi login:
The ‘CIA’ seem to be running an older firmware release – anyone want to let them know? 😉
Chatty Devices
Some devices and firmware love to talk. I mean, take a look at this Polycom device – it’s happy to tell us its life story before we’ve even logged on.
\xff\xfb\x01\x00\xff\xfd\x03\x00\x0d\x0a\x0d\x0aHi, my name is : Anderson Industries\x0d\x0a\x0d\x0aSerial Number: 006961\x0d\x0aBrand: Polycom\x0d\x0aSoftware Version: Release 7.5.4 - 04 Mar 2005\x0d\x0aModel: VS\x0d\x0aNetwork Interface: ISDN_UNKNOWN\x0d\x0aMP Enabled: No\x0d\x0aIP Address: 10.10.10.50\x0d\x0aGMT: Sun Nov 20 06:13:07 2016\x0d\x0aTime In Last Call: 0:02:34\x0d\x0aTotal Time In Calls: 3926:29:17\x0d\x0aTotal Calls: 10417\x0d\x0aCountry Code: 1\x0d\x0a
A lot of devices and firmware grab the system name and/or locations and spit it out in the banner responses before log-on. Not inherently a bad thing (I mean security through obscurity is no security at all, right?) but it does make it easier for attackers to know who they’re attacking.
\x0d\x0aWANFleX Access Control 0\x0d\x0aAdidas_Borisovskoe1\x0d\x0a\x0d\x0a\xff\xfb\x01\xff\xfe\x22\xff\xfd\x03\xff\xfd\x1f\x0dLogin:\x0d\x1b[6C\x1b[K\x0d\x1b[6C
Vigilante Devices
So this was an interesting one. There are botnets out there logging in to insecure devices with default usernames and passwords and changing them to something non-default in order to prevent them being attacked by malicious botnets. There are a small number of these devices on the internet so far; 3,659 revealed in my scans.
This one seems to be created by Team White and the anti-botnet…botnet is called REINCARNA. You can read more about this on their GitLab page.
\x0aREINCARNA / Linux.Wifatch\x0a\x0aYour device has been infected by REINCARNA / Linux.Wifatch.\x0a\x0aWe have no intent of damaging your device or harm your privacy in any way.\x0a\x0aTelnet and other backdoors have been closed to avoid further infection of\x0athis device. Please disable telnet, change root/admin passwords, and/or\x0aupdate the firmware.\x0a\x0aThis software can be removed by rebooting your device, but unless you take\x0asteps to secure it, it will be infected again by REINCARNA, or more harmful\x0asoftware.\x0a\x0aThis remote disinfection bot is free software. The source code\x0ais currently available at https://gitlab.com/rav7teif/linux.wifatch\x0a\x0aTeam White \[email protected]\x3e\x0a\x0a
This one is a little less subtle but the outcome is the same:
\xff\xfb\x01\xff\xfb\x03\xff\xfd\x18\xff\xfd\x1f\x0d\x0aYour security sucks! Use less obvious passwords and stop having telnet listen from the whole world!\x0d\x0aNothing has been done in these routers except changing the motd, rebooting them or issuing configure replace startup-config will remove this.\x0d\x0aBut first, go fix your network!\x0d\x0a\x0d\x0a\x0d\x0aUser Access Verification\x0d\x0a\x0d\x0aPassword: \x0d\x0a% Password: timeout expired!\x0d\x0aPassword:
Older Devices/Firmware
It should be of no surprise that there are really old devices still sitting on the internet. This is a problem that won’t be going away any time soon but it’s still worth looking at some interesting stats…
- The device with the longest up-time I’ve seen is 5.6 years. To this day I still see sysadmins boasting about their up-times; sometimes even posting screenshots and shell outputs to public forums. In most cases, your up-time is just an indicator for the last time you patched your systems system… and that’s not a good thing.
- The oldest firmware I saw was from 1997-2001. Again, this problem of old crap on the internet isn’t going away any time soon unfortunately.
Amusing Devices/Firmware
As I was trawling through the data I came across some… funny banners.
\xff\xfb\x01\x0a\x0d\x0a\x0d\x0a\x0dWelcome to UTMA.com\x0a\x0d\x0a\x0dUnauthorized use of this device is prohibited.\x0a\x0d\x0a\x0dTrespassers will be shocked via the keyboard interface.\x0a\x0d\x0a\x0d\x0a\x0d\x0a\x0d\x0a\x0dUsername:
Actually… I couldn’t really tell if this one was meant to be funny or not:
\xff\xfb\x01\x0d\x0aWARNING: CONTENTS UNDER PRESSURE. HIGHLY FLAMMABLE. RISK OF SHOCK.\x0d\x0a DO NOT ATTEMPT TO OPEN COVER. NO USER SERVICABLE PARTS INSIDE.\x0d\x0a REFER SERVICING TO QUALIFIED PERSONNEL ONLY.\x0d\x0a\x0d\x0a Unauthorized access is prohibited and will be prosecuted by law.\x0d\x0a\x0d\x0alogin :
Have fun with my IP address, NASA.
\x0aWelcome to the blackhole. \x0aYour ip adress was saved and will be sent to nasa.\x0a
Interesting Banners
Damnit why the hell am I seeing projectors on the internet?!
\x0d\x0aSHARP XG-C435X Version 1.01.\x0d\x0a(c) 2007 Sharp Corporation.\x0d\x0a\x0d\x0aUser Name:
Telnet is not available on port 23 so why don’t you go ahead and look at this .gif (why is it even a .gif?!) which will tell you what port to connect to… my head hurt after seeing this one…
\x0aTelnet is not available on port 23.\x0a\x0aSee http://m5.chicago.il.us/telnet.gif\x0a\x0d\x0a
There was a small number of these Intelligent Power Meters – a mere clear-text password away from remotely turning off power?
\x0a\x0dGW25 v1.6.21 - Intelligent Power Meters GPRS Gateway\x0a\x0dDeveloped by Satelitech S.A for ESG Dilec\x0a\x0dEnter password:
Here’s an automatic number plate recognition system by PIPS Technology who have been exposed in the past.
\x0aATZ\x0d\x0aP372 application Aug 29 2008 16:07:45\x0d\x0aP372 Serial Number: 6169\x0d\x0apcb:1, vers:03, rel:x06, build:1159\x0d\x0aRAM: 128M @ 128M\x09EPROM: 512k\x0d\x0aFlex capabilities 003f\x0d\x0a Camera firmware: 4.34\x0a 362 epld vers: 13\x0a ANPR enabled for: USA Louisiana , 2271\x0a Operating system: C EXECUTIVE 3.3\x0aeprom image checksum: 1408\x0a application crc: bf68\x0a current config crc: f8f7\x0areference config crc: f8f7\x0a* Installed options: 00200018\x0a* ... Compact Flash\x0a* ... Basic VES with no security\x0a* ... USA Licenceplate recognition\x0a* PIPS Technology AUTOPLATE (tm) license plate recognition\x0a* VES - (violation enforcement system)\x0a\x3e\x3e
There are GAMES running on Telnet!!! I guess I’m not old enough to have known that this was/still is a thing!
I certainly admire the effort.
Here’s chess:
Welcome to the INTERNET CHESS CLUB\x0d\x0a\x0d\x0aweb: www.chessclub.com email: [email protected]\x0d\x0aphone: 1-412-436-5558\x0d\x0a\x0d\x0alogin:
And another – you gotta have some Telnet Chess competition, right?
\x0a\x0d _ __ __ __ \x0a\x0d | | / /__ / /________ ____ ___ ___ / /_____ \x0a\x0d | | /| / / _ \x5c/ / ___/ __ \x5c/ __ `__ \x5c/ _ \x5c / __/ __ \x5c\x0a\x0d | |/ |/ / __/ / /__/ /_/ / / / / / / __/ / /_/ /_/ /\x0a\x0d |__/|__/\x5c___/_/\x5c___/\x5c____/_/ /_/ /_/\x5c___/ \x5c__/\x5c____/ \x0a\x0d ^^__ _____________________ _ _ _ \x0a\x0d / - \x5c_ / ____/ _/ ____/ ___/ _ | || || |\x0a\x0d \x3c| __\x3c / /_ / // / \x5c__ \x5c (_) |_______|\x0a\x0d \x3c| \x5c / __/ _/ // /___ ___/ / _ \x5c__ ___ /\x0a\x0d \x3c| \x5c /_/ /___/\x5c____//____/ (_) |___|_|\x0a\x0d \x3c|______\x5c |_|___|\x0a\x0d _|____|_ ====================================== |___|_|\x0a\x0d (________) freechess.org ---- 167.114.65.195 (_______)\x0a\x0d /________\x5c ====================================== /_______\x5c \x0a\x0d (Login screen designed by Alefith)\x0a\x0d\x0a\x0d ****** Welcome to the Free Internet Chess Server at freechess.org ******\x0a\x0d\x0a\x0dWebpage: http://www.freechess.org\x0a\x0dHead admin : Chessty Complaints to : [email protected]\x0a\x0dServer location: freechess.org Server version : 1.25.20\x0a\x0d\x0a\x0d If you are not a registered player, enter guest or a unique ID.\x0a\x0d (If your return key does not work, use cntrl-J)\x0a\x0d\x0a\x0dlogin:
“An on-line real time multiplayer text based role-playing game”
\x0a\x0d17 players on.\x0a\x0dSystem started 4 days and 2 hours ago.\x0a\x0dGetting site info...\x0a\x0d\x0a\x0d-------------------------------------------------------------------------------\x0a\x0d Thanks to: Michael Seifert, Hans Henrik Strfeldt, Tom Madsen,\x0a\x0d Katja Nyboe, Alan Button, Eric Litman, and Peter Bartlett\x0a\x0d For many ideas and starting us down this twisting road of imagination.\x0a\x0d-------------------------------------------------------------------------------\x0a\x0d http://www.theforestsedge.com\x0a\x0d _____ _ _____ _ _ _____ _ \x0a\x0d|_ _| |__ ___ | ___|__ _ __ ___ ___| |_( )___ | ____|__| | __ _ ___ \x0a\x0d | | | \x27_ \x5c / _ \x5c | |_ / _ \x5c| \x27__/ _ \x5c/ __| __|// __| | _| / _` |/ _` |/ _ \x5c\x0a\x0d | | | | | | __/ | _| (_) | | | __/\x5c__ \x5c |_ \x5c__ \x5c | |__| (_| | (_| | __/\x0a\x0d |_| |_| |_|\x5c___| |_| \x5c___/|_| \x5c___||___/\x5c__| |___/ |_____\x5c__,_|\x5c__, |\x5c___|\x0a\x0d |___/\x0a\x0d\x0a\x0d [1] Start a new character\x0a\x0d [2] View online players\x0a\x0d [3] Recover lost password\x0a\x0d [4] Request character list\x0a\x0d [5] Help with connection problems\x0a\x0d\x0a\x0d --* Or enter the name of an already existing character. *--\x0a\x0d\x0a\x0d Choice:
I also happened to see a lot of non-telnet services responding on port 23. Most of them are probably the result of misconfigurations or an attempt at really bad obscurity.
- 16,674 banners appeared to be HTTP responses
- 8,118 banners appeared to be SSH
- 2,112 banners appeared to be FTP servers (Microsoft FTP Service,FileZilla, etc)
- 40 banners appeared to be VNC servers
Final Words
It’s 2017 and we still have millions,maybe tens of millions of devices on the internet with default credentials listening on inherently insecure services. Millions of devices where credentials are being passed around in clear-text. Devices that probably have no reason to be on the internet at all like projectors and printers. It’s not a problem that will go away any time soon unfortunately and I don’t know that there is a clear solution for it either.
Network operators and administrators need to work harder to keep their infrastructures secure – there’s a lot of enterprise level equipment out there just waiting to be owned.
Firmware manufacturers also need to start shipping their devices with more secure, default configurations.
Is this all wishful thinking? I hope not…